The Third Network
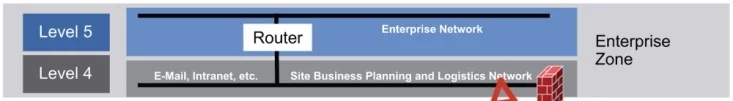
As we see wireless devices and applications become an integral part of the landscape in the industrial arena there is a growing concern for what layer of the network should wireless devices be placed. This question should concern you since this may impact your plant or plant operations in the future. We typically see two physical networks in most plants which are referred to as the Process Control Network (PCN) and Business Network (BN). The PCN is within layer 3 and below and the BN is layer 4 based on the Purdue model shown in figure 1.
Fig. 1 – Purdue reference model for Control hierarchy (from Rockwell Automation)
If you are part of the plant team that supports either of these networks, these discussions have been or will be ongoing for your organization. We have seen some of the major companies already stake out where wireless devices will fall and under what level of the network. As a company that deploys wireless networks and helps plan wireless networking, we have seen many approaches over the last several years in the deployment of wireless devices in the industrial space.
Why should you be concerned which layers each of the wireless devices connect to and what impact will this have to your site?
You have a need to deploy sensors and / or handhelds. What layers should these devices be deployed under?
Hopefully during the reading of this article, we can help address these questions.
Let us look at the different layers that make up a typical industrial network looking at components of the Purdue Model.
Layer 1, 2 and 3 (PCN)
This is commonly referred to as the Process Control Network (PCN) and where most of the major Distributed Control Systems (DCS), PLCs, and Field Devices reside. This has always been seen as the “Holy of Holy” with access into this layer as sacred, as it should be.
This is a very time sensitive network where communication from field devices to the control consoles must not be impacted and where emergency shutdown systems as well as other time critical devices are located. The PCN layer requires careful planning for patches, firmware, or new releases along with comprehensive testing of these changes with little to no outages. This usually falls under the Process Safety Management processes, so you must adhere to strict change control processes that may impact existing systems. The PCN is considered a 24/7 network and no outage is allowed unless it a planned and these are typically rare.
This seems like a logical area for most of the Wireless Sensor Network (WSN) devices to connect into the network. These type of sensor networks are still considered a point to point solution since they normally are their separate wireless network, using protocols, such as WiHart, Zigbee or other proprietary protocols. They may deploy mesh network technology but they perform a single function and usually are tied back to the PCN via a gateway.
What impact do these types of devices have into this layer? Very little if your support staff monitor and maintain these devices and have access into the PCN network. However, these devices will require firmware updates, etc as new releases are deployed and as you deploy different vendors’ solutions these start posing additional risks as you increase the numbers of applications servers / workstations that are required to be deployed, maintained and / or monitored. You can visualize, as you increase the number of islands of point to point applications this starts to increases your risk in this physical layer.
What if you want applications such as tablets or handhelds that allow outside operators or maintenance personnel to perform rounds and create work orders? Or perhaps adding wireless process video cameras and even implementing VoIP communication that can reduce your operating costs for your plant?
As we move from the point to point wireless applications to typical 802.11 (WiFi) and or 802.16(WiMax) wireless networks, we now enter the forbidden layer and know that these applications most likely will require Layer 4 or Business System access which imposes additional risks, such as traffic congestion and security risks to our PCN layers.
The security policy for most PCNs restrict data from outside the PCN firewall thus restricting the use of the business applications referred to above. Some companies believe that you should restrict 802.11 from the PCN network due to security risk, while we believe the network physical layers pose just as much risk as a well-designed wireless network.
One solution as we are seeing with some companies, is deploying two devices at the same locations for the PCN and BN when deploying 802.11 WiFi devices. This approach allows the separation of the data but increases the complexity of your wireless spectrum, determining rogue devices, clients, etc. and this does not even address the increase of maintenance and installation costs.
As most Corporations are implementing security polices, deploying devices and monitoring these devices, this provides unique challenges if you deploy your devices under the PCN and you deploy this same type of monitoring for the Layer 4 devices. You may have to create a new physical layer for your local support team so they can monitor both layers of wireless device systems. Most control vendors provide this solution under the PCN layers. What if your knowledge base for these types of wireless devices are part of your local IT team?
Big applications rewards such as Voice over IP (VoIP) and Asset location will pose a problem with a layer 2 or 2.5 approach. We are seeing major wireless vendors providing better wireless devices and applications that will help reduce operating cost for two way radios and provide additional safety of personnel with the ability to locate personnel within the plants.
Layer 4 (BN)
This layer is commonly referred to as the Business Network, Plant Network, or the IT Network in industrial facilities. This physical network is either maintained remotely or by a local IT team. Any devices that are attached to this network layer must follow certain security and operating patch policies, which today requires constant updates and upgrades to maintain reliability and a safe network. This layer may contain multiple Virtual Local Area Networks (VLANs) allowing organizations to segment traffic enabling Quality of Service (QoS) for certain applications. If your company has deployed a Voice over IP PBX then they have probably deployed a VLAN network to assure no interruption in your communications. VLANs assist in allowing multiple critical applications to be segmented avoiding traffic congestion in a well-planned network. Like many large urban cities, a poorly planned highway is just like a poorly planned non-monitored network. When you have too much traffic in a given area, it will cause frustration to the end users and impact these applications. The most common wireless devices and applications today in this layer are the 802.11 (WiFi) that allows employees access while in conference rooms, VoIP wireless handhelds, and 802.16 (WiMAX) that allows you to backhaul or replace fiber between hard to get locations (i.e. contractors’ trailers, turnaround trailers that may require temporary access to your networks).
Layer 4 is usually connected via a Wide Area Network (WAN) to other plant sites, any typically includes corporate and international business units for large corporations. Corporate IT usually maintain these network connections and maintain access into and out from their organization via a firewall or by an outsourced provider. Remote employees or traveling employees may have ability to access their network remotely via different access levels (i.e. VPN and or remote access providers). With this access, very few (if any) can access below Layer 4 or 3.5 devices remotely.
Layer 3.5 (DMZ)–
This layer is commonly referred to as the DMZ of the Process Control Network. This allows the communication to and from systems such as Plant Historians to PCN layers and the same firewall that allows communication from the Business Network to plant historian and other devices that are collecting data from PCN layers. A firewall provides protection to the PCN and restricts access to Layer 3 and 2. The firewall may fall under support of the Plant IT / Corporate IT department or even the Plant Control System Group. No matter which team supports these firewalls there are usually strict policies on what traffic can and should flow outbound or inbound to the PCN layers. We will discuss this layer as this is where we can connect what we refer to as the Third Physical Wireless Network Layer or as some call it, the Wireless Network Layer.
Why Third Network?
No matter what layer you decide is best for your site needs today, it important to know what your future wireless needs and / or applications that your site may deploy. We often make decision on cost today versus the cost of these decisions in tomorrow’s dollars. What if I must move or add applications that impact my maintenance team’s application that was deployed a year ago, can I reuse my investment for additional applications in the future and what is the best layer to place these future applications in? What are our companies’ future wireless plans and what does it look like? Will it impact my project or future applications costs?
As we deployed wireless systems, we saw a need for a separation of the wireless network into what we call the Third Physical Network or Third Network. The need was not that wireless is less secure than a wired network however we saw that implementing wireless sensors / gateways, operator’s handhelds, VoIP devices, process and security video as well as the monitoring and support impacted both the Business Networks and Process Control Networks. As we discussed above the ability to handle multiple wireless devices, maintain different security for different applications was placing a strain on existing infrastructures and posing risks trying to implement these new applications without causing any outages or changes to existing infrastructures.
One example; for some companies who have not implemented VLAN or may have limited use to certain switches, deploying VLANS across all their plant switches may be considered too risky for their existing infrastructure. This usually requires that all switches be at the same firmware level, access manageability into these switches, etc. They may have a mix of different vendor managed switches and even some unmanaged switches that would not allow VLAN or segmenting data unless the unmanaged switches were replaced.
Creating a Third Network layer gives you the ability to implement a solution that allows specific locations to access the PCN layer via the DMZ layer or 3.5 layer and allows secured access to the Business Network or Layer 4 for application such as handheld devices that require access to ERP system or Plant system to access Standard Operating Procedures, etc. This physical layer also allows for the creation of VLANs for additional applications and some customers have added a firewall between the Third network and the DMZ layers.
We have seen companies that have deployed this access gain the ability to leverage remote monitoring and the facilitate the maintenance of the wireless devices and network without compromising performance or risk to the PCN level or Business Network layer thereby increasing their Return of Investment (ROI) for additional applications deployed at this layer.
In conclusion, the Third Network may or may not become part of your strategy for wireless deployment. Our intention was not to create confusion but offer a solution that may help you in your future deployments for your site. If you would like additional information on deployment strategies or how you can get a wireless site plan for your company, please contact I2oT Solutions at sales@I2oTSolutions.com or give us a call at 281-804-0590